Shuttle2X
Safe use of automated shuttle vehicles in urban traffic through supporting infrastructure communication

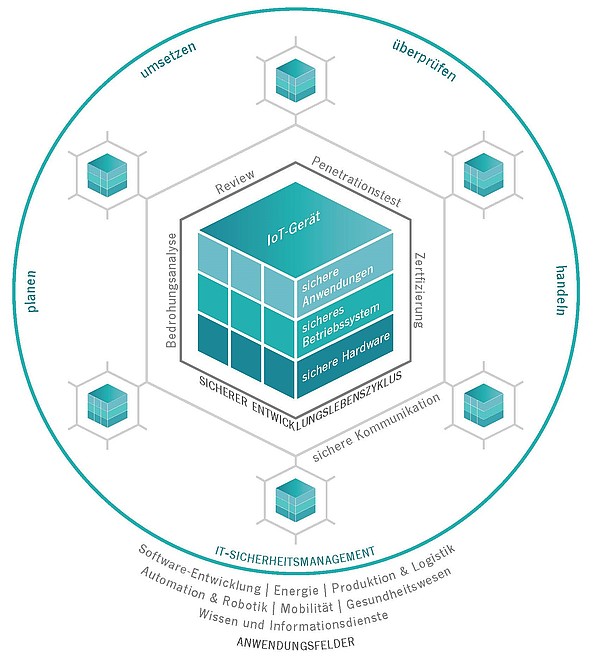
With the Competence Center for IT Security (KIS), the FZI has created a central point of contact for applied IT security research with the support of the state of Baden-Württemberg. The center offers problem-solving expertise in questions of IT security for small and medium-sized enterprises in Baden-Württemberg. At the Competence Center for IT Security, research is conducted on security technologies that are easy to understand and apply.

Ever-advancing digitalization across all industries is making it necessary for IT systems to be increasingly networked. Systems that previously operated in complete isolation are now being connected to the Internet. This leads to a greatly increased attack surface and can enable worldwide attackers to gain access. Particularly worth protecting in this context are critical infrastructures such as power plants or hospitals – attacks on such systems can have serious consequences for the safety of people and the environment.
Likewise, the Internet of Things brings with it new security challenges. To meet these challenges, pure expertise in IT security methods and mechanisms is not enough. The key to success lies in supplementing this knowledge with in-depth expertise of the respective application domain.
Safe use of automated shuttle vehicles in urban traffic through supporting infrastructure communication
Static hardware/software analyses in the context of scalable edge computing platforms
Generating resilient system-on-a-chip architectures for RISC-V
Generation of Side-Channel-Free Software for Embedded Systems